Wachtwoord herstel – Hashcat
Informatie (ENG):
Hashcat is the world’s fastest CPU-based password recovery tool.
While it’s not as fast as its GPU counterpart oclHashcat, large lists can be easily split in half with a good dictionary and a bit of knowledge of the command switches.
Background
Hashcat was written somewhere in the middle of 2009. Yes, there were already close-to-perfect working tools supporting rule-based attacks like “PasswordsPro”, “John The Ripper”. However for some unknown reason, both of them did not support multi-threading. That was the only reason to write Hashcat: To make use of the multiple cores of modern CPUs.
Granted, that was not 100% correct. John the Ripper already supported MPI using a patch, but at that time it worked only for Brute-Force attack. There was no solution available to crack plain MD5 which supports MPI using rule-based attacks.
Hashcat, from its first version, v0.01, was called “atomcrack”. This version was very poor, but at least the MD5 kernel was written in assembler utilizing SSE2 instructions and of course it was multi-threaded. It was a simple dictionary cracker, nothing more. But it was fast. Really fast. Some guys from the scene become interested in it and after one week there were around 10 beta testers. Everything worked fine and so requests for more algorithm types, a rule-engine for mutation of dictionaries, a windows version and different attack modes were added. These developments took around half a year, and were completely non-public.
Then, with version 0.29, “atomcrack” was renamed to “Dr. Hash”. Then with the release of version 0.30 to “hashcat”.
The first official hashcat release was v0.30, released on 24.12.2009.
Starting with hashcat release v0.40, released on 05.08.2012, binaries for Mac OSX were added.
Features
- Multi-Threaded
- Free
- Multi-Hash (up to 24 million hashes)
- Multi-OS (Linux, Windows and OSX native binaries)
- Multi-Algo (MD4, MD5, SHA1, DCC, NTLM, MySQL, …)
- SSE2, AVX and XOP accelerated
- All Attack-Modes except Brute-Force and Permutation can be extended by rules
- Very fast Rule-engine
- Rules compatible with JTR and PasswordsPro
- Possible to resume or limit session
- Automatically recognizes recovered hashes from outfile at startup
- Can automatically generate random rules
- Load saltlist from external file and then use them in a Brute-Force Attack variant
- Able to work in an distributed environment
- Specify multiple wordlists or multiple directories of wordlists
- Number of threads can be configured
- Threads run on lowest priority
- Supports hex-charset
- Supports hex-salt
- 90+ Algorithms implemented with performance in mind
- … and much more
Attack-Modes
- Straight *
- Combination *
- Toggle-Case
- Brute-Force
- Permutation
- Table-Lookup
- PRINCE
Algorithms
- MD5
- md5($pass.$salt)
- md5($salt.$pass)
- md5(unicode($pass).$salt)
- md5($salt.unicode($pass))
- HMAC-MD5 (key = $pass)
- HMAC-MD5 (key = $salt)
- SHA1
- sha1($pass.$salt)
- sha1($salt.$pass)
- sha1(unicode($pass).$salt)
- sha1($salt.unicode($pass))
- HMAC-SHA1 (key = $pass)
- HMAC-SHA1 (key = $salt)
- MySQL323
- MySQL4.1/MySQL5
- phpass, MD5(WordPress), MD5(phpBB3), MD5(Joomla)
- md5crypt, MD5(Unix), FreeBSD MD5, Cisco-IOS MD5
- MD4
- NTLM
- Domain Cached Credentials, mscash
- SHA256
- sha256($pass.$salt)
- sha256($salt.$pass)
- sha256(unicode($pass).$salt)
- sha256($salt.unicode($pass))
- HMAC-SHA256 (key = $pass)
- HMAC-SHA256 (key = $salt)
- md5apr1, MD5(APR), Apache MD5
- SHA512
- sha512($pass.$salt)
- sha512($salt.$pass)
- sha512(unicode($pass).$salt)
- sha512($salt.unicode($pass))
- HMAC-SHA512 (key = $pass)
- HMAC-SHA512 (key = $salt)
- SHA-512(Unix)
- Cisco-PIX MD5
- Cisco-ASA MD5
- WPA/WPA2
- Double MD5
- bcrypt, Blowfish(OpenBSD)
- MD5(Sun)
- md5(md5(md5($pass)))
- md5(md5($salt).$pass)
- md5($salt.md5($pass))
- md5($pass.md5($salt))
- md5($salt.$pass.$salt)
- md5(md5($pass).md5($salt))
- md5($salt.md5($salt.$pass))
- md5($salt.md5($pass.$salt))
- md5($username.0.$pass)
- md5(strtoupper(md5($pass)))
- md5(sha1($pass))
- Double SHA1
- sha1(sha1(sha1($pass)))
- sha1(md5($pass))
- sha1($salt.$pass.$salt)
- MD5(Chap), iSCSI CHAP authentication
- SHA-3(Keccak)
- Half MD5
- Password Safe SHA-256
- IKE-PSK MD5
- IKE-PSK SHA1
- NetNTLMv1-VANILLA / NetNTLMv1-ESS
- NetNTLMv2
- Cisco-IOS SHA256
- Android PIN
- AIX {smd5}
- AIX {ssha256}
- AIX {ssha512}
- AIX {ssha1}
- GOST, GOST R 34.11-94
- Fortigate (FortiOS)
- OS X v10.8 / v10.9
- GRUB 2
- IPMI2 RAKP HMAC-SHA1
- sha256crypt, SHA256(Unix)
- Drupal7
- WBB3, Woltlab Burning Board 3
- scrypt
- Cisco $8$
- Cisco $9$
- Radmin2
- Django (PBKDF2-SHA256)
- Cram MD5
- SAP CODVN H (PWDSALTEDHASH) iSSHA-1
- Plaintext
- Joomla < 2.5.18
- PostgreSQL
- osCommerce, xt:Commerce
- Skype
- nsldap, SHA-1(Base64), Netscape LDAP SHA
- nsldaps, SSHA-1(Base64), Netscape LDAP SSHA
- Oracle 11g/12c
- SMF > v1.1
- OS X v10.4, v10.5, v10.6
- EPi
- Django (SHA-1)
- MSSQL(2000)
- MSSQL(2005)
- PeopleSoft
- EPiServer 6.x < v4
- hMailServer
- EPiServer 6.x > v4
- SSHA-512(Base64), LDAP {SSHA512}
- OS X v10.7
- MSSQL(2012 & 2014)
- vBulletin < v3.8.5
- PHPS
- vBulletin > v3.8.5
- IPB2+, MyBB1.2+
- Mediawiki B type
- WebEdition CMS
- Redmine Project Management Web App
Commandolijn opties
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 |
hashcat, advanced password recovery Usage: hashcat [options] hashfile [mask|wordfiles|directories] ======= Options ======= * General: -m, --hash-type=NUM Hash-type, see references below -a, --attack-mode=NUM Attack-mode, see references below -V, --version Print version -h, --help Print help --eula Print EULA --expire Print expiration date --quiet Suppress output * Benchmark: -b, --benchmark Run benchmark * Misc: --hex-salt Assume salt is given in hex --hex-charset Assume charset is given in hex --runtime=NUM Abort session after NUM seconds of runtime * Files: -o, --outfile=FILE Define outfile for recovered hash --outfile-format=NUM Define outfile-format for recovered hash, see references below --outfile-autohex-disable Disable the use of $HEX[] in output plains -p, --separator=CHAR Define separator char for hashlists/outfile --show Show cracked passwords only (see --username) --left Show uncracked passwords only (see --username) --username Enable ignoring of usernames in hashfile (Recommended: also use --show) --remove Enable remove of hash once it is cracked --stdout Stdout mode --potfile-disable Do not write potfile --debug-mode=NUM Defines the debug mode (hybrid only by using rules), see references below --debug-file=FILE Output file for debugging rules (see --debug-mode) -e, --salt-file=FILE Salts-file for unsalted hashlists * Resources: -c, --segment-size=NUM Size in MB to cache from the wordfile -n, --threads=NUM Number of threads -s, --words-skip=NUM Skip number of words (for resume) -l, --words-limit=NUM Limit number of words (for distributed) * Rules: -r, --rules-file=FILE Rules-file use: -r 1.rule -g, --generate-rules=NUM Generate NUM random rules --generate-rules-func-min=NUM Force NUM functions per random rule min --generate-rules-func-max=NUM Force NUM functions per random rule max --generate-rules-seed=NUM Force RNG seed to NUM * Custom charsets: -1, --custom-charset1=CS User-defined charsets -2, --custom-charset2=CS Example: -3, --custom-charset3=CS --custom-charset1=?dabcdef : sets charset ?1 to 0123456789abcdef -4, --custom-charset4=CS -2 mycharset.hcchr : sets charset ?2 to chars contained in file * Toggle-Case attack-mode specific: --toggle-min=NUM Number of alphas in dictionary minimum --toggle-max=NUM Number of alphas in dictionary maximum * Mask-attack attack-mode specific: --pw-min=NUM Password-length minimum --pw-max=NUM Password-length maximum * Permutation attack-mode specific: --perm-min=NUM Filter words shorter than NUM --perm-max=NUM Filter words larger than NUM * Table-Lookup attack-mode specific: -t, --table-file=FILE Table file --table-min=NUM Number of chars in dictionary minimum --table-max=NUM Number of chars in dictionary maximum * Prince attack-mode specific: --pw-min=NUM Password-length minimum --pw-max=NUM Password-length maximum --elem-cnt-min=NUM Minimum number of elements per chain --elem-cnt-max=NUM Maximum number of elements per chain ========== References ========== * Outfile formats: 1 = hash[:salt] 2 = plain 3 = hash[:salt]:plain 4 = hex_plain 5 = hash[:salt]:hex_plain 6 = plain:hex_plain 7 = hash[:salt]:plain:hex_plain 8 = crackpos 9 = hash[:salt]:crackpos 10 = plain:crackpos 11 = hash[:salt]:plain:crackpos 12 = hex_plain:crackpos 13 = hash[:salt]:hex_plain:crackpos 14 = plain:hex_plain:crackpos 15 = hash[:salt]:plain:hex_plain:crackpos * Debug mode output formats (for hybrid mode only, by using rules): 1 = save finding rule 2 = save original word 3 = save original word and finding rule 4 = save original word, finding rule and modified plain * Built-in charsets: ?l = abcdefghijklmnopqrstuvwxyz ?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ ?d = 0123456789 ?s = !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ ?a = ?l?u?d?s ?b = 0x00 - 0xff * Attack modes: 0 = Straight 1 = Combination 2 = Toggle-Case 3 = Brute-force 4 = Permutation 5 = Table-Lookup 6 = Prince * Hash types: 0 = MD5 10 = md5($pass.$salt) 20 = md5($salt.$pass) 30 = md5(unicode($pass).$salt) 40 = md5($salt.unicode($pass)) 50 = HMAC-MD5 (key = $pass) 60 = HMAC-MD5 (key = $salt) 100 = SHA1 110 = sha1($pass.$salt) 120 = sha1($salt.$pass) 130 = sha1(unicode($pass).$salt) 140 = sha1($salt.unicode($pass)) 150 = HMAC-SHA1 (key = $pass) 160 = HMAC-SHA1 (key = $salt) 200 = MySQL323 300 = MySQL4.1/MySQL5 400 = phpass, MD5(Wordpress), MD5(phpBB3), MD5(Joomla) 500 = md5crypt, MD5(Unix), FreeBSD MD5, Cisco-IOS MD5 900 = MD4 1000 = NTLM 1100 = Domain Cached Credentials, mscash 1400 = SHA256 1410 = sha256($pass.$salt) 1420 = sha256($salt.$pass) 1430 = sha256(unicode($pass).$salt) 1440 = sha256($salt.unicode($pass)) 1450 = HMAC-SHA256 (key = $pass) 1460 = HMAC-SHA256 (key = $salt) 1600 = md5apr1, MD5(APR), Apache MD5 1700 = SHA512 1710 = sha512($pass.$salt) 1720 = sha512($salt.$pass) 1730 = sha512(unicode($pass).$salt) 1740 = sha512($salt.unicode($pass)) 1750 = HMAC-SHA512 (key = $pass) 1760 = HMAC-SHA512 (key = $salt) 1800 = SHA-512(Unix) 2400 = Cisco-PIX MD5 2410 = Cisco-ASA MD5 2500 = WPA/WPA2 2600 = Double MD5 3200 = bcrypt, Blowfish(OpenBSD) 3300 = MD5(Sun) 3500 = md5(md5(md5($pass))) 3610 = md5(md5($salt).$pass) 3710 = md5($salt.md5($pass)) 3720 = md5($pass.md5($salt)) 3810 = md5($salt.$pass.$salt) 3910 = md5(md5($pass).md5($salt)) 4010 = md5($salt.md5($salt.$pass)) 4110 = md5($salt.md5($pass.$salt)) 4210 = md5($username.0.$pass) 4300 = md5(strtoupper(md5($pass))) 4400 = md5(sha1($pass)) 4500 = Double SHA1 4600 = sha1(sha1(sha1($pass))) 4700 = sha1(md5($pass)) 4710 = sha1($salt.$pass.$salt) 4800 = MD5(Chap), iSCSI CHAP authentication 5000 = SHA-3(Keccak) 5100 = Half MD5 5200 = Password Safe SHA-256 5300 = IKE-PSK MD5 5400 = IKE-PSK SHA1 5500 = NetNTLMv1-VANILLA / NetNTLMv1-ESS 5600 = NetNTLMv2 5700 = Cisco-IOS SHA256 5800 = Android PIN 6300 = AIX {smd5} 6400 = AIX {ssha256} 6500 = AIX {ssha512} 6700 = AIX {ssha1} 6900 = GOST, GOST R 34.11-94 7000 = Fortigate (FortiOS) 7100 = OS X v10.8 / v10.9 7200 = GRUB 2 7300 = IPMI2 RAKP HMAC-SHA1 7400 = sha256crypt, SHA256(Unix) 7900 = Drupal7 8400 = WBB3, Woltlab Burning Board 3 8900 = scrypt 9200 = Cisco $8$ 9300 = Cisco $9$ 9800 = Radmin2 10000 = Django (PBKDF2-SHA256) 10200 = Cram MD5 10300 = SAP CODVN H (PWDSALTEDHASH) iSSHA-1 99999 = Plaintext * Specific hash types: 11 = Joomla < 2.5.18 12 = PostgreSQL 21 = osCommerce, xt:Commerce 23 = Skype 101 = nsldap, SHA-1(Base64), Netscape LDAP SHA 111 = nsldaps, SSHA-1(Base64), Netscape LDAP SSHA 112 = Oracle 11g/12c 121 = SMF > v1.1 122 = OS X v10.4, v10.5, v10.6 123 = EPi 124 = Django (SHA-1) 131 = MSSQL(2000) 132 = MSSQL(2005) 133 = PeopleSoft 141 = EPiServer 6.x < v4 1421 = hMailServer 1441 = EPiServer 6.x > v4 1711 = SSHA-512(Base64), LDAP {SSHA512} 1722 = OS X v10.7 1731 = MSSQL(2012 & 2014) 2611 = vBulletin < v3.8.5 2612 = PHPS 2711 = vBulletin > v3.8.5 2811 = IPB2+, MyBB1.2+ 3711 = Mediawiki B type 3721 = WebEdition CMS 7600 = Redmine Project Management Web App |
Benchmark
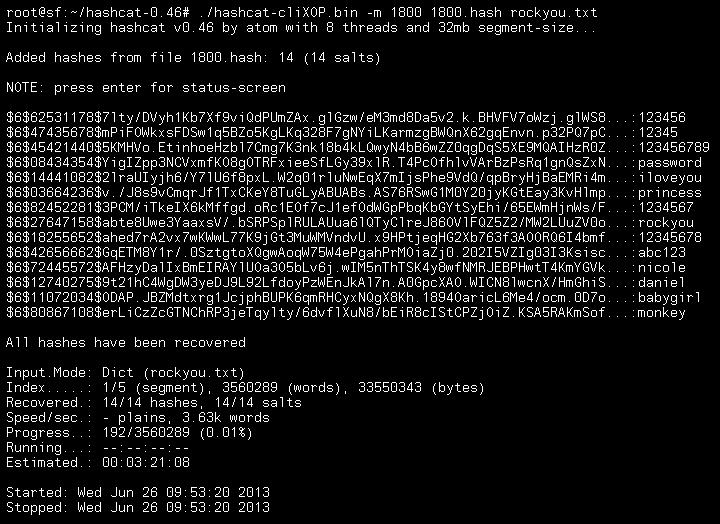
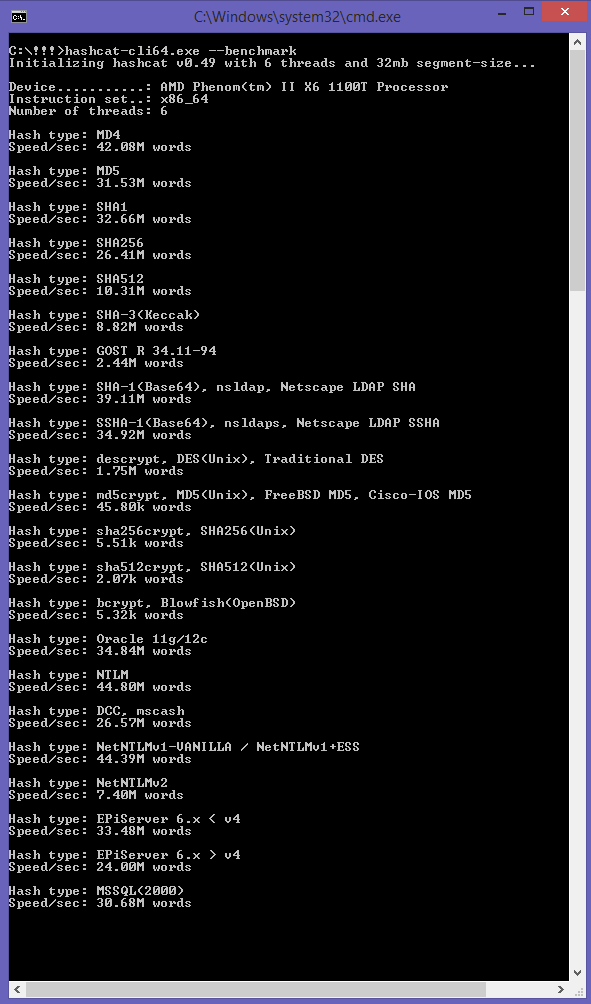
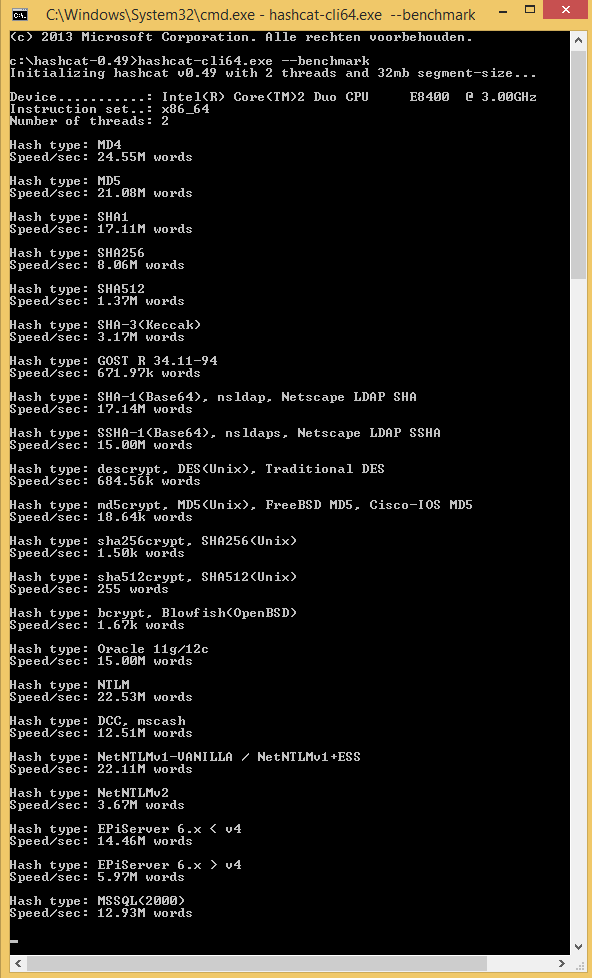
Ik heb het zelf op 2 computers geprobeerd met --benchmark , zit zijn de benchmark resultaten:
Wat heb je nodig?
Zet bijvoorbeeld wachtwoord databanken in een map (in de hashcat folder) genaamd “dicts“, sla de hashes op die je wilt achterhalen in hash.txt, en gebruik het volgende commando:
hashcat-cli64.exe hash.txt dicts